FBI and Dutch Police Target Botnet of Hacked Routers in Global Cybercrime Operation
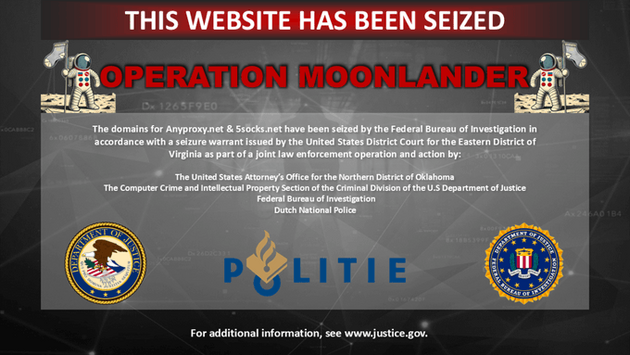
The FBI, in partnership with Dutch police, has successfully shut down a notorious botnet exploiting hacked internet-connected devices, including routers, for cybercriminal activities. This action, known as Operation Moonlander, resulted in the seizure of two proxy services, Anyproxy and 5Socks, accused of distributing botnet access to criminals. The takedown is part of a larger, ongoing effort by international law enforcement to curb the rise of online cybercrimes powered by compromised devices.
How the Botnet Operated: An Inside Look at the Cybercriminal Scheme
At the heart of this botnet operation were four individuals—three Russians and one Kazakhstan national—who used vulnerable wireless routers to build a massive proxy network. By exploiting outdated router models with known security flaws, these cybercriminals took control of thousands of devices worldwide. They then sold access to this botnet, using Anyproxy and 5Socks to mask the IP addresses of criminals conducting illicit activities. Residential proxy networks, like the ones operated by the botnet, are often used to bypass restrictions, but in this case, they were employed for far more nefarious purposes.
FBI and Dutch Police Shut Down Anyproxy and 5Socks Proxy Networks
Both Anyproxy and 5Socks, which had been operating since 2004, were publicly seized on May 7, 2025, with notices from the FBI and Dutch police displayed on their websites. These services were marketed as legitimate tools for accessing geoblocked content, but investigators uncovered a darker side. Through these networks, cybercriminals were able to maintain anonymity while committing illegal activities such as password spraying, DDoS attacks, and ad fraud. The investigation reveals that more than $46 million was allegedly made from the illegal sale of botnet access.
Cybercriminals Exploit Vulnerable Routers for Financial Gain
The four individuals indicted in the case, including Alexey Viktorovich Chertkov, Kirill Vladimirovich Morozov, Aleksandr Aleksandrovich Shishkin, and Dmitriy Rubtsov, are accused of using compromised routers to create a vast network of proxies. These proxies, comprised of residential IP addresses, provided criminals with a much-needed layer of anonymity. This made it harder for online security systems to trace their illegal activities back to the perpetrators. As a result, many unsuspecting users became unwitting participants in the botnet, with their routers hijacked to serve malicious purposes.
The Impact of Operation Moonlander: A Step Toward Cybercrime Prevention
The takedown of Anyproxy and 5Socks sends a clear message about the increasing collaboration between international law enforcement agencies to fight online crime. As highlighted by cybersecurity experts like Ryan English from Black Lotus Labs, these botnets are not just a minor nuisance—they enable a wide range of serious cybercrimes. From financial fraud to sophisticated DDoS attacks, the services provided by these proxy networks were integral to the operations of many online criminals.
Protecting Your Devices from Becoming Part of a Botnet
The dismantling of this botnet is a significant victory in the fight against cybercrime, but it also serves as a reminder for internet users to safeguard their devices. Keeping routers and other internet-connected devices up to date with the latest security patches can help prevent them from being compromised by hackers. As law enforcement continues to target cybercriminal networks, individuals must remain vigilant to ensure their devices are not being exploited for illicit purposes.
𝗦𝗲𝗺𝗮𝘀𝗼𝗰𝗶𝗮𝗹 𝗶𝘀 𝘄𝗵𝗲𝗿𝗲 𝗿𝗲𝗮𝗹 𝗽𝗲𝗼𝗽𝗹𝗲 𝗰𝗼𝗻𝗻𝗲𝗰𝘁, 𝗴𝗿𝗼𝘄, 𝗮𝗻𝗱 𝗯𝗲𝗹𝗼𝗻𝗴. We’re more than just a social platform — from jobs and blogs to events and daily chats, we bring people and ideas together in one simple, meaningful space.